EDI via AS2
EDI via AS2 (Applicability Statement 2) is one of the most widely used and secure methods of transmitting Electronic Data Interchange (EDI) documents over the internet. This page provides a comprehensive overview of how AS2 works, its benefits, technical components, and why it’s the preferred protocol for many global businesses.
What is AS2?
AS2 is popular communication protocol used for secure and reliable data delivery between businesses over the internet, most often in EDI (Electronic Data Interchange) scenarios. AS2 is a mechanism to transport data through an envelope signed digitally and encrypted to guarantee confidentiality, data integrity and authentication during this transmission.
Unlike classic file transfer solutions, AS2 offers a variety of data types and real time delivery confirmations via MDNs. It’s cost-effective, it eliminates the use of a VAN (value added network) and allows end user to communicate with another end user.
Although AS2 is secure and highly efficient, companies still have to deal with operational headaches like managing certificates, setting up firewalls, and maintaining connections with a variety of partners. These hurdles can now be overcome by next-generation B2B integration platforms that offer central configuration and simplify ongoing AS2 operations and creates an incredible opportunity for AS2 in today’s connected supply chains.
Understanding AS2 and EDI
EDI is the structured transmission of data between organizations by electronic means and it is used to transfer electronic documents. Instead of paper or email, EDI allows businesses to send purchase orders (EDI 850), invoices (EDI 810), and shipping notices (EDI 856) directly from one system to another, cutting back on manual data input, processing turnaround time, and errors.
However, in order for EDI to be efficient, a secure and reliable means of transmitting is required, and that is where AS2 steps in.
How Does AS2 Work?
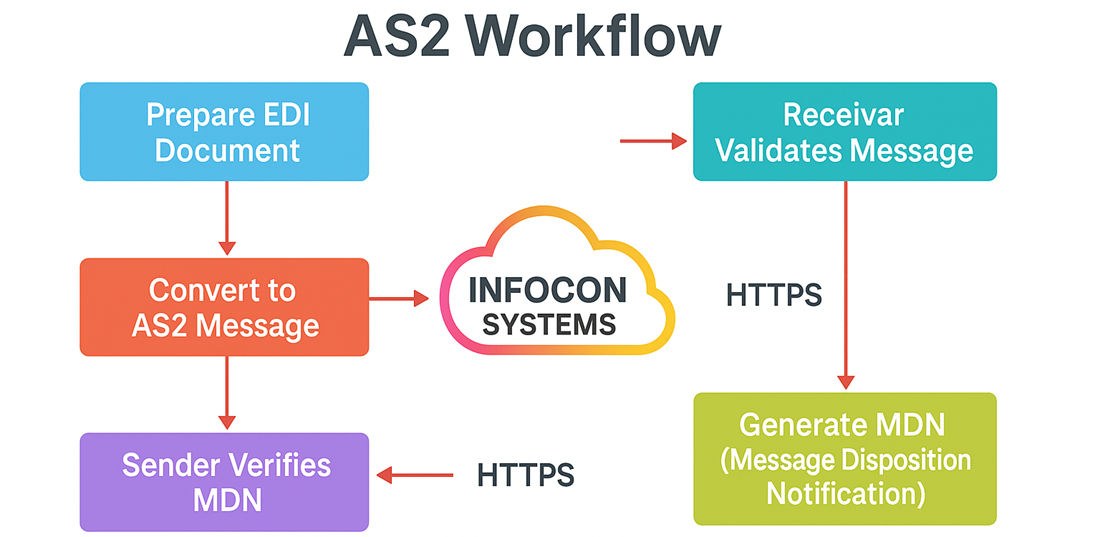
You require a pair of systems for an AS2 connection: a server and a client that interconnect directly over the internet, utilizing a point-to-point connection. Each system has an AS2-compliant application and is uniquely identified with the AS2 ID. Before your actual data is sent, AS2 wraps the file in an “envelope” secured by S/MIME. The digital envelope may be digitally signed in order to authenticate the sender, and encrypted using digital certificate so that the contents cannot be read by others.
Once the file is well packaged, it is transmitted over HTTPor HTTPS to the receiver’s AS2 endpoint. The receiver, on the other hand, decrypts the message (if it was encrypted), validates the digital signature, and extracts the plain text document. This is in order to ensure that the data hasn't been tampered with on its way, and really originated form the person it was meant to originate from.
After it is received and validated, the recipient returns a MDN. (If you can read it this email is your proof your message was received and processed correctly) The MDN can be transmitted immediately after that or later, via another connection. If there is any problem with the file, like invalid signature, the MDN reports an error.
AS2 is highly valued for its strong security features, compliance with data exchange standards, and ability to provide non-repudiation, meaning the recipient cannot deny receiving the message. It is commonly used in industries like retail, logistics, and manufacturing, where companies need reliable, traceable, and secure communication. By using AS2, businesses can bypass expensive third-party networks and transmit sensitive data directly and efficiently over the internet.
History of AS2
AS2 was established in early 2000s by the IETF to facilitate safe and efficient sending of business documents over the internet. It became popular once Walmart required its suppliers to use it, replacing expensive VANs with encrypted internet file exchange with added receipt notification (MDN) and digital signatures.
What are the Attributes of the AS2 Protocol
AS2 provides a set of capabilities that make it a reliable and secure way to transmit business documents over the internet.
Security: It encrypts data and applies digital signatures for data security and sender assertion.
Reliability: Guarantees delivery of messages using MDNs (Message Disposition Notifications).
Non-repudiation: Ensures that the recipient of a message cannot deny sending the message.
Standards-Based: Complete implementation with support for HTTP(S) and S/MIME to ensure compatibility.
Compression Support: Can compress the message for faster transmission.
Interoperability: It is a means to facilitate communication among different software and systems.
Automation-Ready: Compatible with EDI and ERP systems for automatic data transfer.
Affordable: Cheap alternative to VANs, sends data over the internet.
What Are AS2 Certificates?
AS2 certificates are digital certs used to secure and authenticate communication between trade partners in AS2 (Applicability Statement 2) data exchange. These certificates are used in the encryption and decryption and digital signing of AS2 messages in order to ensure data is kept confidential, authentic and integral.
There are two common uses for AS2 certificates:
Encryption/Decryption: When a sender sends an AS2 message, it encrypts the message using the public key of the receiver. Only the recipient, in possession of the appropriate private key, can decrypt and read the message. This is done so that no one can intercept the message or read it.
Digital Signing/Verification: The AS2 message can be signed digitally with a private key of the AS2 sender to verify authorship and the content of the AS2 message. The recipient now checks whether the message has not been tampered with on the way, and also whether it really originated from whoever is claiming it did, and uses the sender’s public certificate to do so.
What Are AS2 Message Types?
AS2 protocol consists of a set of messages that cooperate to allow authorised, authenticated and auditable document exchange between trading partners. Each of the message types has a specific function in the transfer of data.
AS2 Payload Message - This is the message itself that carries the business content, e.g. a purchase order, an invoice, a shipping notification (usually an EDI document). The payload is ultimately protected in the S/MIME standard manner, possibly including encryption and digital signature to provide secrecy and authenticity. This message is sent using HTTPS to the receiver's AS2 endpoint.
Synchronous MDN (Message Disposition Notification): After AS2 message is received and processed, the synchronous MDN is an immediate response delivered over the same connection. This signals that the message was successfully delivered, decrypted correctly and passed validation. Such a MDN is informed real time back to the sender.
Asynchronous MDN: Instead of a synchronous MDN, an asynchronous MDN is sent after through a second HTTP connection. This is most commonly used for in highcommunication, slowprocessing environments where the receiver requires time to process the message before replying. It still does the same thing—tells you what got delivered and prevents denial. Signed Message (AS2 only): Message can have a digital signature that authenticates the sender and guarantees that the message was not changed in the transmission process. In many compliance oriented spaces, signing is seen as a must-have.
Encrypted Message: The message is encrypted so only the recipient can read the content of the message. AS2 also allows strong encrypting algorithms to be used to ensuring sensitive business information cannot be compromised in transit.
The combined functionality of these message types and features enables AS2 to provide a secure, standards-based internet exchange method for EDI and business documents which ensures full traceability and legal delivery proof.
Industries That Rely on AS2
AS2 is commonly used in:
Retail & eCommerce: Required by partners like Walmart, Amazon, and Target.
Manufacturing & Distribution: For supply chain automation.
Logistics & Transportation: For real-time shipment and status updates.
Healthcare: For HIPAA-compliant document exchange.
What is needed for AS2 Integration?
To set up EDI via AS2, you will require: AS2-compliant EDI tool (e.g., Infocon Systems) Digital Certificates for encryption and authentication AS2 Identifiers for you and your partner AS2 URLs for Send and Receive activities Mutual Configuration between trading partners.
Key Benefits of Using AS2 for EDI
AS2 provides a secure, efficient, and cost-effective solution for exchanging EDI documents, making it a preferred choice for modern B2B communications.
Data Security: Messages data and delivery are encrypted and digitally signed.
MDN Acknowledgment: Provides evidence that the file has been delivered, and integrity, that it was not tampered with in transport.
Internet-Based: Eliminates the need for traditional Value-Added Networks (VANs).
Standards-Compliant: Used by leading retailers and ERP systems globally.
Cost-Effective: Saves money by giving the option of direct partner communication.
Automated Workflow: Enables real-time, unattended data exchange between systems.
This sounds awesome. How do I implement EDI for my business?
Give us a call at 1-888-399-0722 or request a quote for an easy EDI setup.



